Security Information
Brilliance CRM offers a security architecture that meets, and exceeds, industry standards that is designed to protect sensitive data and ensure the privacy of your business. We utilize AES-256 encryption, the industry standard for data security, to secure fields and databases, safeguarding them against unauthorized access. For password protection, Brilliance CRM employs Argon2, an award-winning, highly secure hashing algorithm, ensuring that user credentials are securely encrypted and resistant to brute-force attacks. Additionally, the system integrates Ed25519 for digital signatures, providing a fast and secure method for verifying the authenticity and integrity of documents.
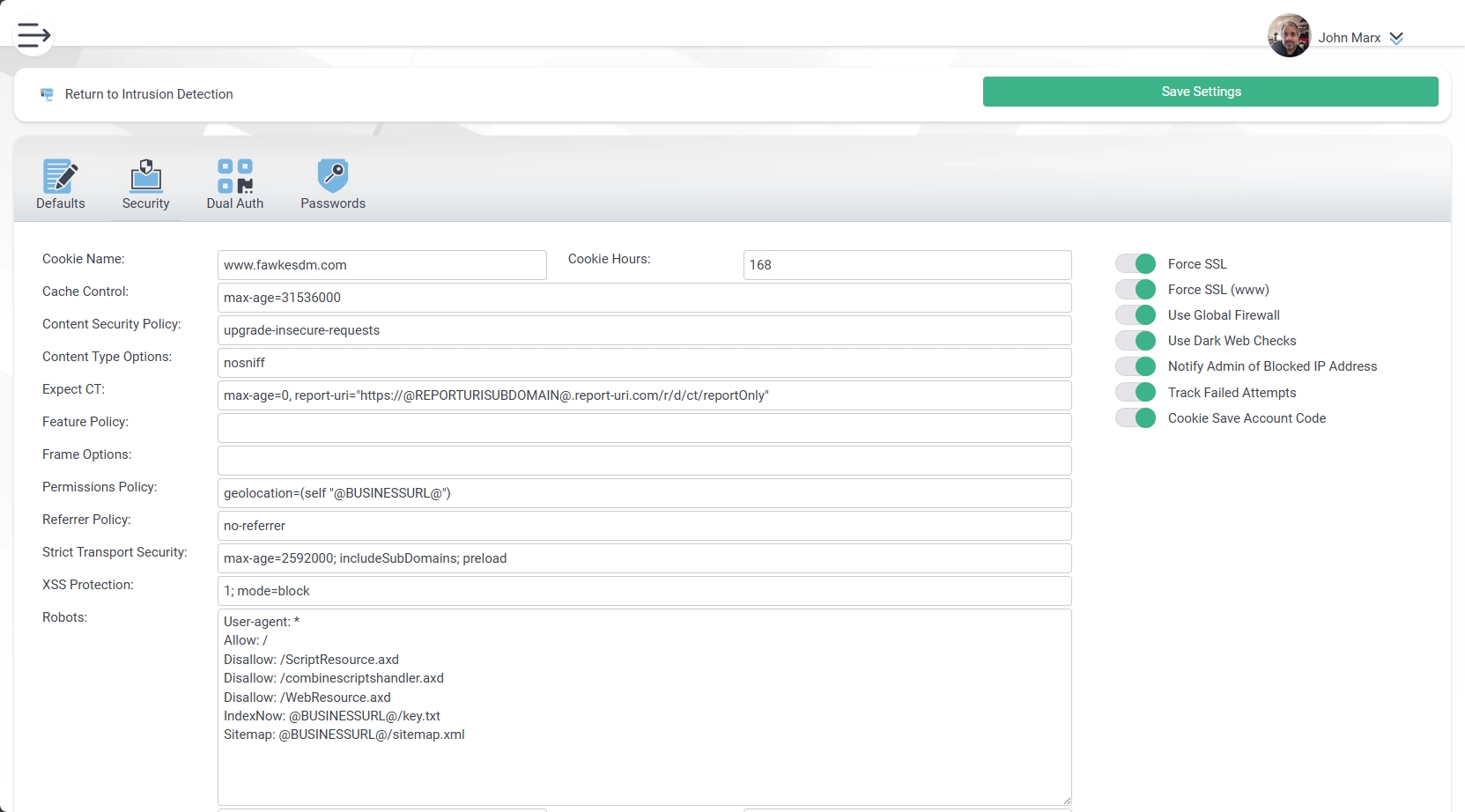
To further enhance security, Brilliance CRM is equipped with both local and global firewalls that monitor and control incoming and outgoing network traffic, protecting against potential cyber threats. Two-factor authentication adds an extra layer of security, requiring not only a password but also a second factor to verify user identity. Moreover, users have the ability to customize page headers, adding another layer of security to protect web pages from common vulnerabilities and attacks. These comprehensive security measures make Brilliance CRM a secure choice for managing sensitive business data.
Key Features For Security
- Set the number of login attempts per IP address before automatic lock.
- Define the automatic lock timeout period (before automatic unlock).
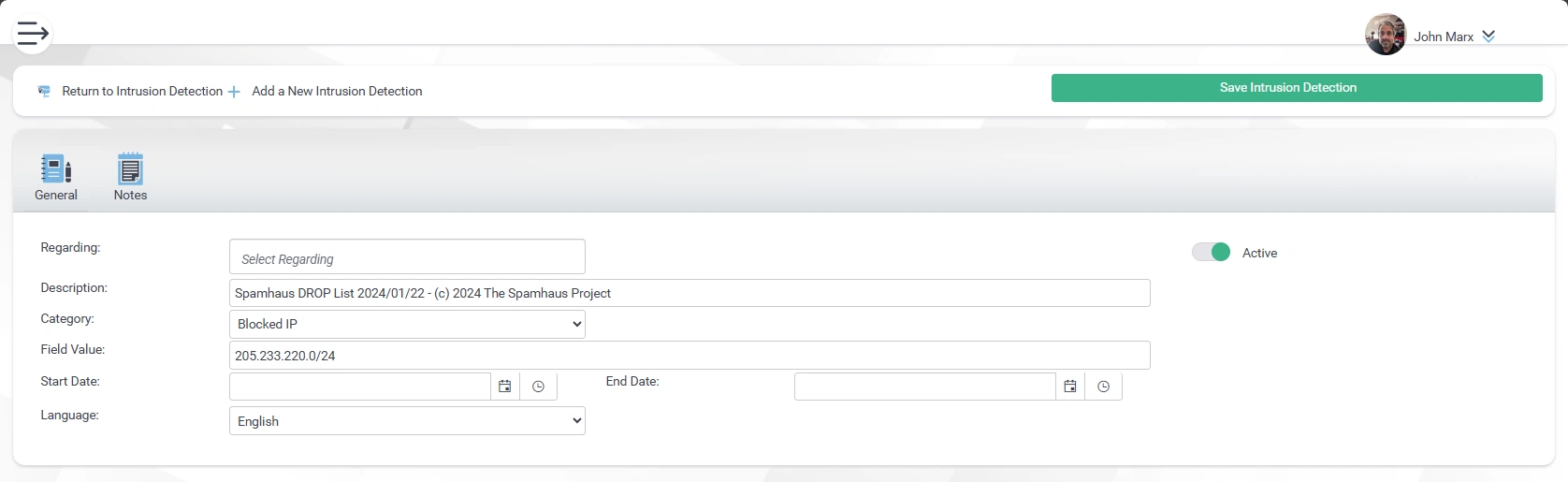
- Intrusion Detection
- Ability to block passwords that are common to better secure your users passwords
- Manual IP address block (permanent)
- Ability to assign a list of "bad words" that block spam from forms
- Block country of the user
- IP addrsss range blocks using CIDR (e.g., 1.2.3.4/24)
- CIDR is the short for Classless Inter-Domain Routing and is used to explain a range of IP addresses.
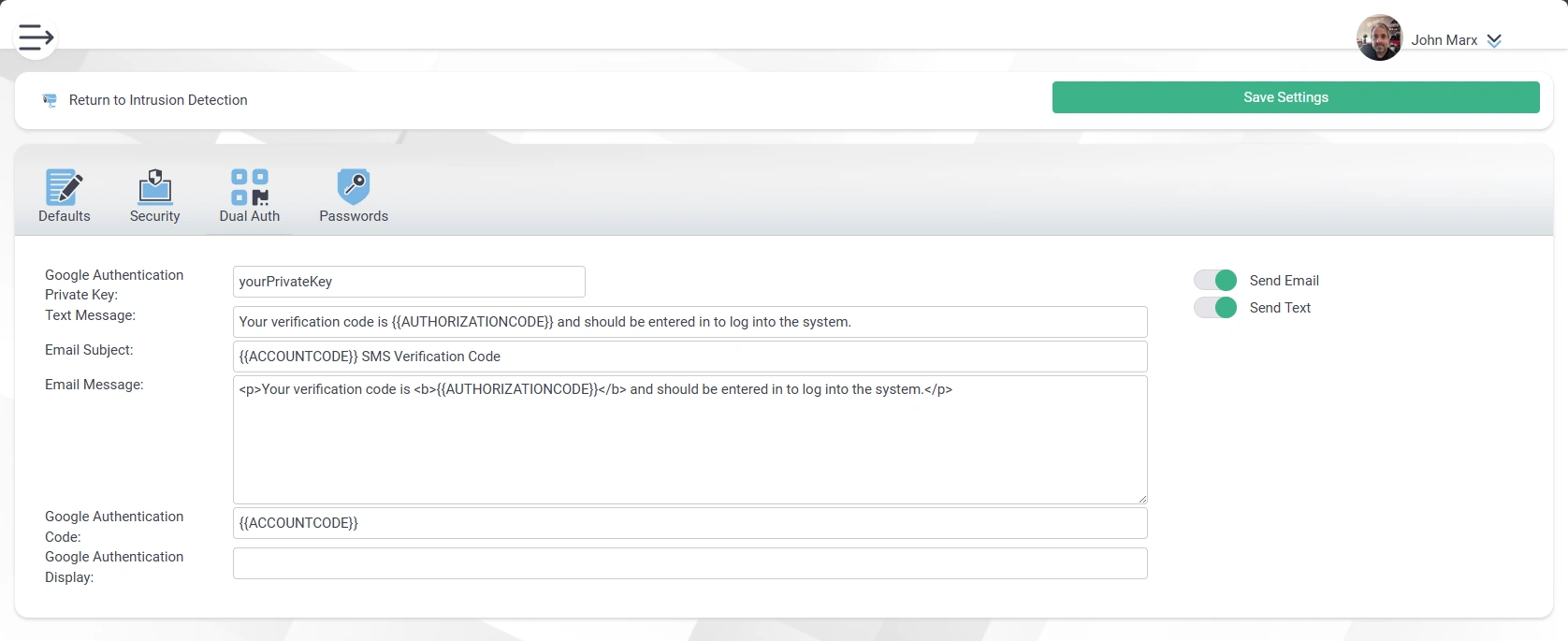
- Two Factor Authorization (2FA or TFA) with Google Authenticator.
- Multi-Factor Authentication (MFA).
- Force all pages and links to use SSL (TLS).
- Enable a Global Firewall which incorporates our distributed honeypots.
- Notifications
- Logins, Logouts, and Change Passwords
- Blocked Country, IP Address
- Notification of Failed Logins
- Robots.txt file.
- Security.txt file.
- All databases are fully AES-256 encrypted (Encrypts data both at rest and in transit).
- Control Cookie Information and Expirations.
- Microsoft Azure network.
- Daily Backups (on-site and off-site).
- Logging within all modules to the level you set (minimal to HIPPA level [Enhanced Logging]).
- Zero trust for all modules.
- All items a user doesn't have access to are hidden and/or disabled based on the purpose of the item.
- Single Database Per Customer: Each customer has their own separate instance of the software and datbase infrastructure. This means no tenant shares databases with another tenant. This approach offers the highest level of data isolation and security, making it ideal for clients with stringent data privacy and regulatory requirements. Within the tenant everything is equally separated based on the users granular user security group level.
- Page Headers
- Cache Control
- Content Security Policy
- Content Type Options
- Expect CT
- Feature Policy
- Frame Options
- Referrer Policy
- Strict Transport Policy
- Dark Web notifications of your email address existing on the dark web, what sites, and links so you can update/remove your information.
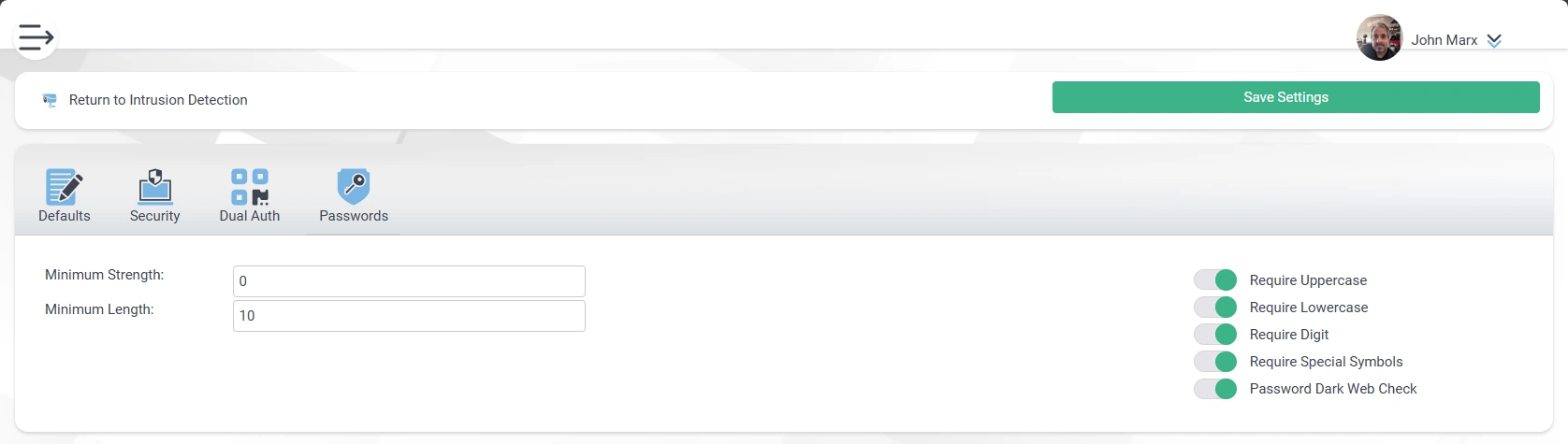
- Passwords
- Minimum Length specification
- Options Available To Be Set
- At least one UPPERCASE character
- At least one lowercase character
- At least one digit character (0 through 9)
- At least one symbol character (special characters like !, @, #, $, %, ^, &, *, (, ), etc.)
- Minimum Strength (from 0 to 100) (based on our password generator [e.g., https://www.fawkesdm.com/Apps/Password/])
- User Security Groups (Role-Based Access Control or RBAC)
- Unlimited Groups
- Multiple groups can be assigned to users
- Easily see who is in each group
- All passwords are secured with Argon2 with customized salt, per user.
- All custom fields and fields that contain personal information encrypted with AES-256, different password with salt, per database record meeting the needs of HIPPA out of the box.
- All forms are digitally signed using Ed25519 and have used as part of the court process.
- Penetration testing done monthly.
- 24x7x365 Monitoring of infrastructure, servers, hardware, and the uptime of your site.
- Strict access where Brilliance, Inc. does not have access to your data without specific authorization.